BACKGROUNDIn the old days (Windows 2000 and Windows 2003) an Active Directory domain could only have one password and account lockout policy per domain for domain accounts.
The group policy with the password settings had to be linked at the domain level(common method people used was to set the policy in the default domain policy).
What options where there if you wanted a different policy for certain users or certain groups? For example what if you wanted service accounts to have a stricter policy? There were not many options. Organizations could try and create their own filter (not recommended) or use a third party tool (not native, not cheap, and needs plenty of testing).
In some cases organizations would create a new domain because they wanted different policies. I was never involved in a new domain just for a password policy but I've heard of it happening.
PASSWORD POLICIES IN WINDOWS 2008Microsoft introduced a new feature in Windows 2008 called
Fine Grained Password Policies (FGPP). The domain functional level has to be at Windows 2008 for this feature to work.
FGPP's allowed organizations to specify multiple password policies within a single domain. You can use fine-grained password policies to apply different restrictions for password and account lockout policies to different sets of groups and users in a domain.
The link above is a step by step guide for configuring FGPP's. There are also some other good FGPP references that I refer to.
As you can see in Florian and Sean's great blog entries setting up fine-grained passwords was not the easiest thing to do. Admins had to use ADSI Edit to configure it and the entire process was not admin/user friendly.
There were some third party tools that could make this process easier but again that involved another tool.
WINDOWS SERVER 8 FGPP IMPLEMENTATIONAs noted in my
previous post there are a lot of improvements in Windows Server 8. Once again a feature is now exposed using the Active Directory Administrative Center (ADAC).
To start open ADAC and navigate to the System container. From there navigate to the Passwords Settings Container and right click and select New > Password Settings
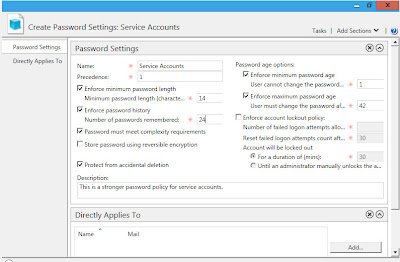
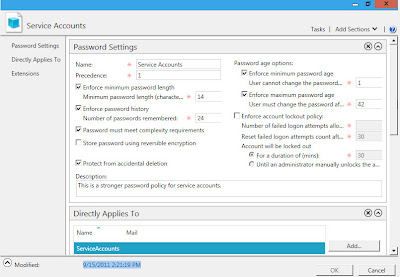
As you can see I named my Password Setting Object(PSO) and I set a precedence level. Precedence is used if there are multiple PSO's applied, the lower precedent will win. I'd try to limit the number of PSO's in a domain.
I've set the minimum length at 14 which is more stringent/strict compared to my normal domain policy which is 8 characters. I want the service accounts to have stronger passwords.
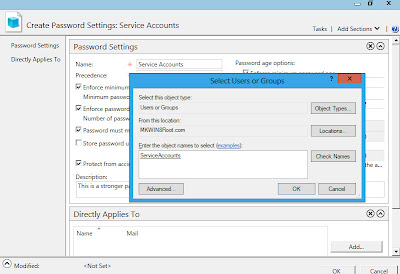
Next I'm going to select "Add" in the Directly Applies to box. In this example I am going to apply the PSO to a group named ServiceAccounts. I could have also selected user accounts here.
Once I'm done with creating and applying the PSO to the group I can verify that the password is set. I navigate to my Service account user that is a member of the ServiceAccount group. I right click and select "View resultant password settings"
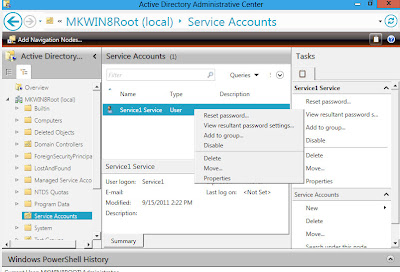
The resultant password setting box is presented. It returns the Service Accounts PSO that I created.
There is also another option for user accounts. In ADAC you will notice a Password Settings pane.
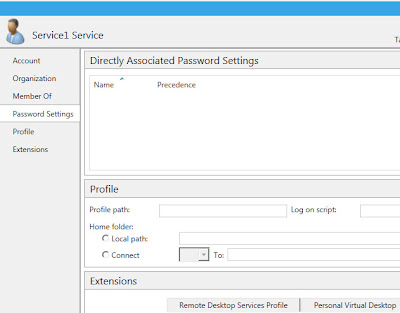
PSOs can be directly assigned to user accounts. I'd recommend using groups when possible but the option is there.
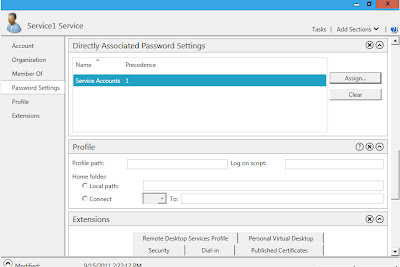
So now the PSO is created in applied...but does it work. Can I still use an 8 character password for this account? If it worked correctly the 8 character password should no longer be accepted. I tried a 10 character complex password
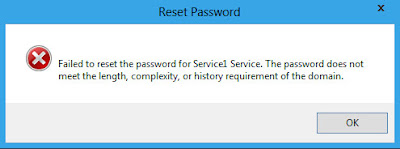
Success Full Success!! It would be nice if the error message was more verbose. For example telling the user that they need a 14 character password based off the PSO settings.
One other area I think admins will continue to ask for is the ability to have a different password policy per OU (not just users and groups).
They can't get every feature into every release but this is a huge step forward. Nice job Microsoft AD Team! I think this will help organizations and now more folks will use FGPP. (just remember the domain functional level has to be at 2008 or higher)
Also remember this is a pre-Beta release so things can change. Having said that Steve Ballmer said over 500,000 copies have already been downloaded....the WIndows 8 buzz is on for sure :)


































































